Introduction
During the past couple of weeks, we have seen a rise in public abuse of Shadowbrokers’ leaked exploits allegedly used by the NSA, a handful of these exploits target windows operating system and gives attackers the ability to reliably penetrate into windows boxes! Eternalblue is the name of the exploit that targeted SMB 445 port on windows operating systems that gave you RCE, it was patched by Microsoft a couple of days before the leak but many systems were left vulnerable over the internet, in addition to that, windows XP and 2003 which are no longer supported by Microsoft didn’t receive any fixes until recently. This allowed malware authors to abuse vulnerable systems to mine cryptocurrencies (Adylkuzz) and spread ransomware (WannaCry).
Now after almost a week it seems like either people have patched their systems or have had their system compromised and gradually the number of vulnerable systems will decrease, but there’s more to this story. Eternalblue wasn’t the only windows exploit in the pile of leaked exploits by Shadowbrokers. Another vulnerability that we think is also important and should be addressed as soon as possible before it starts being abused and exploited widely is named Esteemaudit, there’s no denying the fact that it has to be already abused in the wild and it’s about time WannaCry and Adylkuzz like malware switch to this exploit. Fortinet analyzed the technical aspects of this exploit here.
Esteemaudit, RDP Exploit Affecting Windows XP and Windows Server 2003
This exploit targets Remote Desktop Protocol, specifically smart card authentication feature. By exploiting this vulnerability, the attacker can bypass the authentication mechanism and gain access to the operating system, since the issue most likely won’t be addressed by Microsoft, we have to look for configuration options to disable this feature and mitigate the vulnerability where upgrading the operating system is not an option. Referring to Rapid7, Esteemaudit is one of the 3 exploits leaked by Shadowbrokers that aren’t addresses by a patch and will have a long lasting impact.
For the first phase, we addressed vulnerable IP addresses in Iran. We scanned Iran’s known IP range and found 23571 addresses with port 3389 (RDP) open. We then analyzed 11655 IPs due to our limited resources and then filtered these systems by the operating system since we were only interested in XP and 2003 boxes, we then looked for the ones that were either a domain controller or part of a domain because we knew for sure by default they have smart card authentication enabled which makes them vulnerable to Esteemaudit exploit. We found 30 vulnerable XP boxes and 394 windows 2003 ones.
We argue that the impact of this vulnerability is huge since people that are still using XP and 2003 boxes in a domain structure must be relying on some sort of legacy software that prevents them from upgrading to newer operating systems, the fact that these boxes are joined in a domain enables the attacker to move laterally and infect all the systems inside the network that are running XP and Windows 2003. Hence, we infer that these systems are vital to organizations and are costlier to maintain and upgrade, factors like downtime and migration of vital legacy software can be causes affecting this issue.
While looking for XP and 2003 systems, we also found several ATM systems with RDP exposed to the internet, we didn’t test any further to see if they were test environments, honeypots or actual ATMs.
Report Structure
The rest of this report is structured as follows:
- Attack surface: We take a brief look at the number of web facing and publicly available Windows XP and 2003 systems that can potentially be vulnerable (depends on RDP being accessible from the internet and smart card authentication being enabled), we then analyze these numbers for Iran with more precision.
- Finding Vulnerable Systems: We look at MASSCAN as a tool to scan wide range of IP addresses for open RDP port (3389). We then discuss methods used to detect the operating system behind an IP address with open RDP port.
- Mitigation: Under this section, possible workarounds to fix this issue without upgrading the OS will be reviewed.
Attack Surface
We are talking about all Windows XP and Windows Server 2003 operating systems that have RDP exposed to the internet and are part of a domain system or have smart card authentication enabled, comparing this to the number of open smb ports, while there may be more RDP ports exposed to the internet than smb, our statistics from a previous study that was done recently to find boxes that were vulnerable to Eternalblue in Iran, this number is greater for smb, note that we are limited to the boxes that have smart card authentication enabled for Esteemaudit to work. But the fact that those vulnerable to Esteemaudit are most likely part of domain increases the impact of a possible attack.
At this stage, we want to have a rough estimate to see how many vulnerable operating systems are accessible over the internet. There’s this report from netcraft which says about 20% of web facing computers were running windows server 2003 at the time of the study (2015). We also did a more precise scan of Iran’s IP addresses and out of 23571 scanned ip addresses (with 3389 open), we found 1404 systems running Windows Server 2003 and 248 running XP, out of which 394 Windows 2003 servers and 30 XP systems were vulnerable which is around 0.036 % of analyzed addresses.
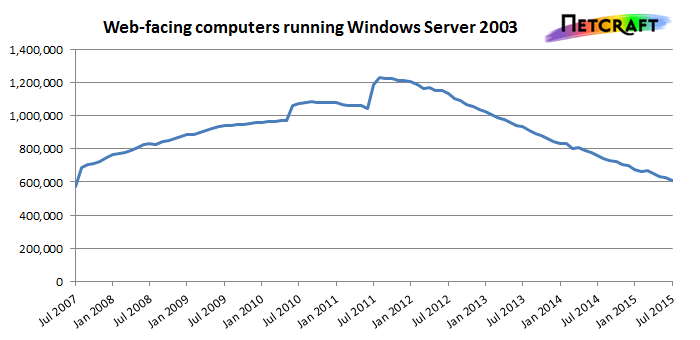
If you add the ease and reliability of this exploit into the mix you’ll realize that this threat can have a huge and long lasting impact, in addition to that, most likely there won’t be any fixes issued as an OS update since XP and 2003 aren’t officially supported anymore by Microsoft.
It’s also worth mentioning that during this study we found a couple of systems belonging to ATMs, we don’t know whether they were honeypots, test environments or actual ATMs being exposed to the internet.
Finding Vulnerable Systems
For this task, we derived Iran’s IP ranges and used masscan to scan for all addresses with port 3389 open. masscan has an nmap like interface, so for example, to scan the whole internet for 3389 TCP port we’ll use the following command (note: this will take forever):
masscan -p3389 0.0.0.0/0
While scanning only Iran’s IP addresses took a while, personal resources are nowhere enough to let us have a wider scan spanning over more IP addresses.
One other challenge we faced was that we had to filter out vulnerable systems, a set of tools came to mind at this point ranging from nmap to custom OS detection and fingerprinting scripts and image processing tricks. We want the method to be lightweight and fast so we tried to find a specific configuration of protocols and parameters specific to RDP for windows XP and 2003, we used rdp-sec-check.pl script but we were out of luck since some of the newer versions of windows operating systems shared the same configurations as XP and 2003. Another option was to use nmap fingerprinting scripts to detect the OS but these scripts take long time and don’t scale well.
The last method that came to our mind was to connect via RDP, take a screenshot and analyze it to detect the underlying OS. I had the experience of sliding windows and finding an image inside another bigger image and I knew it’s rather easy to implement using a library like open-cv.
I did a little bit of research and found rdpy, which is a python library that can handle RDP and is written with twisted, it also happens to have screenshot capability. But in action I found some downsides to this script, twisted error handling is not very well implemented, it gets stuck in loops on some IP addresses and throws errors here and there mostly on XP and 2003 targets. We kept searching for replacements when my colleague found this repo: sticky_keys_hunter. It uses rdesktop linux software to remote desktop and try to test for presence of a specific backdoor which was not of our interest, what was interesting to us though was the fact that it could take screenshots of its remote session, with a little bit of modification we turned this bash script into what we wanted.
The final bundle is available on this repo: DetectOSViaRDP.
- Taking Screenshots
I’ll skip the setup part and go straight to the scripts’ description. We had an IP list from masscan, we stored it in a text file with one address per line:
We use rdpss.sh script to iterate over these IP addresses and take screenshots, you can fine-tune LIMIT variable in rdpss.sh to achieve more parallel sessions (we tested up to 50 and we could test 75 IP addresses per minute on a low end virtual machine).
This script saves the images under ./images directory with their IP addresses as their file names.
- Detecting OS from Screenshot
Now that we have the screenshots, we prepare some small images that are unique to each operating system’s remote desktop screen:
Using open-cv, we search for these images inside taken screenshots. This is done using DetectOS.py.
We passed the directory of all screenshots and our marker image and the script returned the list of IP addresses with that specific image inside their screenshot.
We also manually verified our results over a dataset of 11655 IP addresses for windows XP and 2003 and the result was satisfactory:
FP: 0 %
FN: 0.2 %
Next step was to find out whether the OS was part of a domain or not, sometimes you’ll have to interact with the session and click on “options” button to open the menu that lists the domain name that the system is a part of so we modified our script to send 4 tabs and 1 enter button to achieve this. We used rdesktop and xdotools to achieve this, the original idea came from stickyKeysHunter script.
- Plotting Vulnerable Nodes
We used ipinfodb.com API to get latitudes and longitudes of our scanned IP addresses, we then used gmplot to plot these locations on google map (link).
Mitigation
We were not the only people in the infosec community aware of this threat, while we were preparing our results 0patch came out with a closed source patch which seems to install their proprietary client to mitigate this vulnerability. Couple of days ago a company named enSilo also released a closed source patch (link), they used hot patching to manipulate the in memory winlogon process to fix the vulnerable code.
Update: Our initial analysis made us believe enSilo’s patch is adding itself to browser history for advertisement purposes but it turned out to be wrong, their patch looks innocent, we apologize for this false assumption. There’s also one upside to their solution and it’s that you still get to use smart card authentication and it doesn’t disable the whole feature to mitigate the vulnerability.
We kept doing our research and found a person pointing out to a command that unregisters the vulnerable dll (gpkcsp.dll) under a blog post, shout out to FrankUnderwood2020. It turned out to be a good solution. It does disable smart card authentication but if you are using that you’re screwed anyway. You can unregister this dll and revert to username and passwords which most people are using if you absolutely can’t upgrade the OS.
To run this command you have to have admin privileges, if you don’t it will still tell you it succeeded but vulnerability won’t go away.
regsvr32 /u c:\windows\system32\gpkcsp.dll
To verify it, you can use the following command and you should see this result: ERROR: The system was unable to find the specified registry key or value.
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Gemplus GemSAFE Card CSP v1.0"
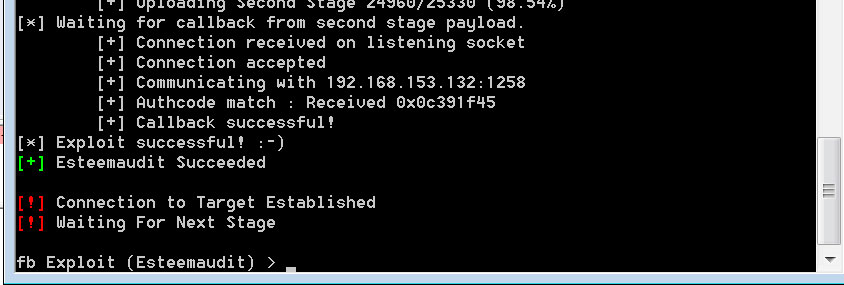
Running the exploit on a vulnerable system:
After unregistering gpkcsp.dll:
This report is a part of telescam project. In this independent/personal project we try to address Telegram messenger scam campaigns and increase public knowledge on their techniques, but since Wannacry had a great impact we also decided to publish a report alongside this project here. Our goal was to increase public knowledge on these issues and try to minimize their impact.
Update (14-June-2017): Microsoft released a patch for Windows XP and Windows Server 2003 operating systems addressing EsteemAudit and other unaddressed exploits by shadowbrokers. Now the best solution if you absolutely can’t upgrade would be to apply official patches.
CVE-2017-0176: EsteemAudit
CVE-2017-7269: ExplodingCan
CVE-2017-8487: EnglishmanDentist