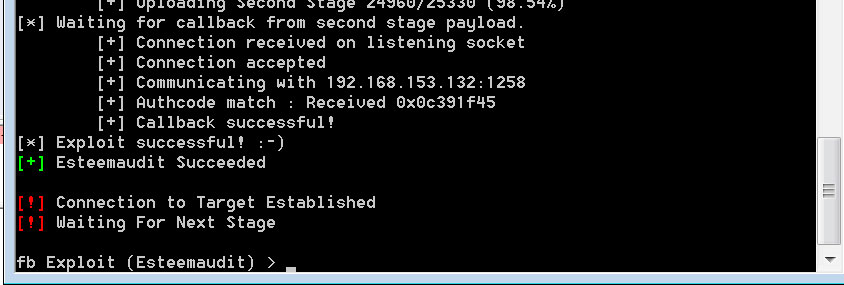
Introduction During the past couple of weeks, we have seen a rise in public abuse of Shadowbrokers’ leaked exploits allegedly used by the NSA, a handful of these exploits target windows operating system and gives attackers the ability to reliably penetrate into windows boxes! Eternalblue is the name of the exploit that targeted SMB 445 port on windows operating systems that gave you RCE, it was patched by Microsoft a couple of days before the leak but many systems were left vulnerable over the internet, in addition to that, windows XP and 2003 which are no longer supported by Microsoft...
Continue reading...Vulnerability
Overview of MAC Algorithms, Fuzzing TLS and Finally Exploiting CVE-2016-7054 Part 1/3
Overview of MAC Algorithms, TLS Protocol and CHACHA20-POLY1305 Algorithms In the upcoming posts I’m going to give an introduction on Openssl CVE-2016-7054 vulnerability and the terminology about this topic. In part 2 we will discuss available tools and techniques and how to actually produce an exploit for this vulnerability, in the 3rd part we will try to enumerate installed Openssl version on our systems and see how we can update software packages that use Openssl like Apache, Nginx and Python. Intro Couple of days ago Fortinet published a blog post titled “Analysis of OpenSSL ChaCha20-Poly1305 Heap Buffer Overflow (CVE-2016-7054)“. A...
Continue reading...Tools for testing HTTPoxy Vulnerability
I’ve developed a script that you can run on your server and test for CGI HTTPoxy vulnerability. It’s available on my github in a repository named HTTPoxy-Test-Tools. I’ve currently developed the script for apache web servers but I’ll be adding support for other webservers gradually. Edit: Added IIS HTTPoxy Testing Tool: https://github.com/silverfoxy/HTTPoxy-Test-Tools/tree/master/iis_httpoxy HTTPoxy Test Tools This tool finds your webserver’s CGI directory, adds a temporary file that returns the HTTP_PROXY environment variable. It then sends a GET request to this CGI file and sets the “proxy” header for the underlying request. If the environment variable is affected, then you’re vulnerable....
Continue reading...HTTPoxy vulnerability affecting CGI Applications
There’s this new vulnerability with a website [HTTPoxy.org] and a logo. Apart from the complete description that’s available at their official website I’m going to walk you through it and give you some practical examples of abuse cases. I’ve also developed a tool that you can run on your servers which tells you if you’re vulnerable or not. What is HTTPoxy and how does it work? HTTPoxy is the name of a vulnerability affecting CGI based applications. This can affect PHP, Go, Python, Perl, etc. Web servers running in a CGI or CGI-like context may assign client request Proxy header...
Continue reading...